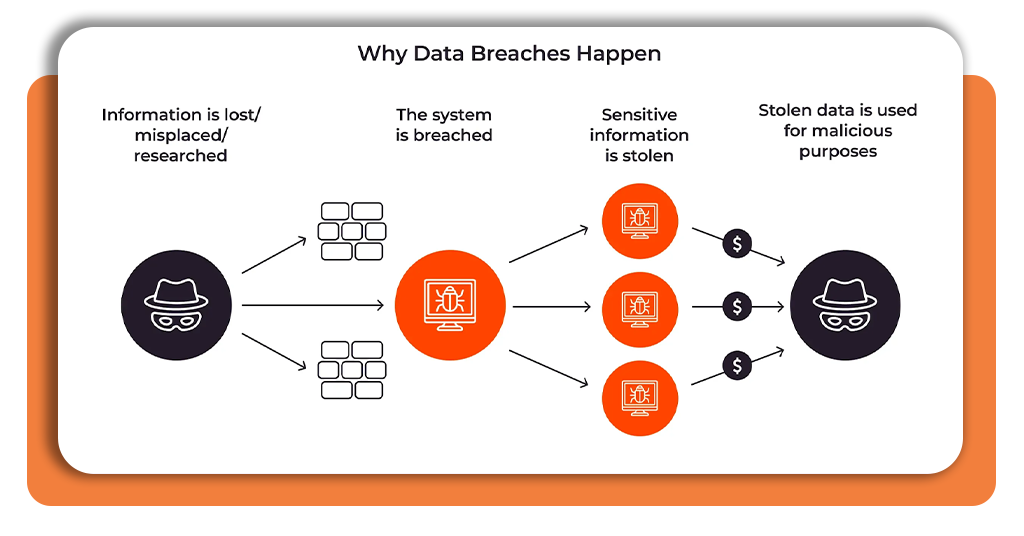
It used to be like watching the news about someone else’s house burning down when you heard about a data breach—it was alarming but far away. Now? It’s basically a monthly subscription service nobody signed up for. Everything has been compromised, sold, or leaked at some point, including your social media accounts, email, and even your pizza delivery account.
The question now is not whether your data is compromised, but rather when and to what extent. What those “we regret to inform you” emails fail to mention is that prepared action is more helpful than panicking. Having a well-thought-out plan before the notification comes is more important when dealing with data breaches than possessing expert hacker skills.
- App Lock - Schützen Sie Ihre privaten Daten mit dieser App
- How to Check Data Usage on iPhone – A Complete Guide
- Wie überprüft man die Datennutzung unter Android? Ein umfassender Leitfaden
How to deal with data breaches step by step
In case you just got that dreaded email from a company you forgot you signed up for, or you’re just wisely preparing for the inevitable, here’s how to handle data breaches like a pro instead of a panicked victim.
Step 1: don’t panic (but do act quickly)
- Verify the breach: check if the notification is legitimate (not a phishing attempt);
- Confirm what data was exposed: passwords, financial info, or just email addresses?;
- Siehe Have I Been Pwned to see which breaches affect you specifically.
Step 2: contain the damage
- Change affected passwords immediately: start with email and financial accounts;
- Enable two-factor authentication everywhere possible;
- Monitor financial accounts for suspicious activity;
- Consider credit freezes if sensitive financial data was exposed.
Die FTC’s breach response guide recommends documenting all steps taken—crucial if legal action follows.
Signs your data was stolen or leaked
You might be compromised if:
- Unfamiliar login alerts arrive from your accounts;
- Password reset emails appear for accounts you didn’t request;
- Friends receive strange messages from your social accounts;
- Small test charges ($0.99–$2.99) appear on your cards;
- You’re locked out of accounts despite using correct passwords.
Less obvious signs:
- Increased spam to previously clean email addresses;
- Personalized phishing emails using your real information;
- New accounts appear on your credit report;
- Unexpected mail from financial institutions.
What to do immediately after a breach
First 24-hour critical actions:
- Secure your email account (the master key to all other accounts);
- Change compromised passwords using strong, unique combinations;
- Contact financial institutions to flag potential fraud;
- Scan devices for malware that might have caused the breach;
- Back up important data in case of ransomware or further attacks.
Nach Angaben von IBM’s research, the first 72 hours determine 90% of breach outcomes—swift action dramatically reduces damage.
Best apps to protect your passwords and identity
Passwords are the adult equivalent of multiplication tables; they are completely useless when there are better ways to remember them.
The best protection apps do more than just save your passwords; they act as your virtual bodyguards, keeping an eye out for dark web leaks, automatically changing compromised credentials, and securing your identity before you even realize something is amiss.
With the help of these tools, breach panic is reduced to a single notification that reads, “I handled it already—go back to your coffee”.
1Password
1Password goes beyond basic password management by monitoring the dark web for your personal information and alerting you to new breaches.
The Watchtower feature automatically flags compromised passwords, weak logins, and vulnerable websites.
Its travel mode temporarily removes sensitive data from your devices when crossing borders, while the digital wallet securely stores payment cards and documents.
Verfügbar für Android und iOS, it generates and autofills complex passwords while keeping everything encrypted.
4.7/5
Dashlane
Dashlane offers one of the most comprehensive breach response systems with its VPN inclusion and real-time dark web monitoring.
The password changer feature automatically updates vulnerable logins across hundreds of popular sites with a single click.
Its identity dashboard provides a security score and personalized recommendations, while the emergency contact feature allows trusted individuals to access your accounts if needed.
Verfügbar für Android und iOS, the built-in VPN protects your connection on public Wi-Fi, making it ideal for frequent travelers.
Have I Been Pwned
While not a traditional protection app, Have I Been Pwned remains the essential free tool for breach awareness.
The service aggregates data from hundreds of breaches, allowing you to check which of your email addresses and passwords have been compromised.
The notification system alerts you when new breaches contain your information, while the password feature lets you check if your passwords have appeared in previous leaks without actually revealing them to the service.
Informationen
Plattformen: Web
Cost: Free
Database: 11+ billion breached accounts
Features: email notifications for new breaches
Final thoughts: breach preparedness is the new normal
Data breaches have moved from rare disasters to regular maintenance events—like digital oil changes for your online life.
The companies storing your data will continue to get hacked, but your response doesn’t have to be chaotic. With the right tools and a clear plan, you can transform from breach victim to breach survivor.
For more password management options, see our password manager apps guide for additional recommendations.





